Diri Security


Diri provides Software as a Service(SaaS) products to our users to solve their business problems. Security is a key component of our offerings and is reflected in our people, processes, and products. This page covers topics like data security, operational security, and physical security to explain how we offer security to our customers.
Organisational security
We are implementing an Information Security Management System (ISMS) that considers our security objectives and the risks and mitigations concerning all the interested parties. We employ strict policies and procedures encompassing the security, availability, processing, integrity, and confidentiality of customer data.
Employee background checks
Each employee undergoes a process of background verification. We do this to verify that we only hire employees trusted to work with our customer’s data. Until this check is performed, the employee is not assigned tasks that may pose risks to our customers.
Security Awareness
Each employee, when inducted, signs a confidentiality agreement and acceptable use policy, after which they undergo training in information security, privacy, and compliance. We provide training on specific security aspects that they may require based on their roles.
We educate our employees continually on information security, privacy, and compliance in our internal community, where our employees check in regularly to keep them updated regarding the organization's security practices. We also host internal events to raise awareness and drive innovation in security and privacy.
Endpoint security
All workstations issued to Diri employees run up-to-date OS versions and are configured with anti-virus software. They are configured to comply with our standards for security, which require all workstations to be correctly configured, patched, tracked, and monitored by Diri's endpoint management solutions. These workstations are secure by default as they are configured to encrypt data at rest, have strong passwords, and get locked when they are idle. Mobile devices used for business purposes are enrolled in the mobile device management system to ensure they meet our security standards.
Physical security
At Workplace
We control access to our resources (buildings, infrastructure, and facilities), where access includes consumption, entry, and utilization with the help of access cards. We maintain access logs to spot and address anomalies.
At Data Centers
Diri does not have its own Data Center. We hire infrastructure from Microsoft Azure through our vendor Crayon.
Monitoring
Our office building is secured through CCTV cameras deployed according to local regulations. Back-up footage is available up to a certain period, depending on the requirements for that location.
Infrastructure security
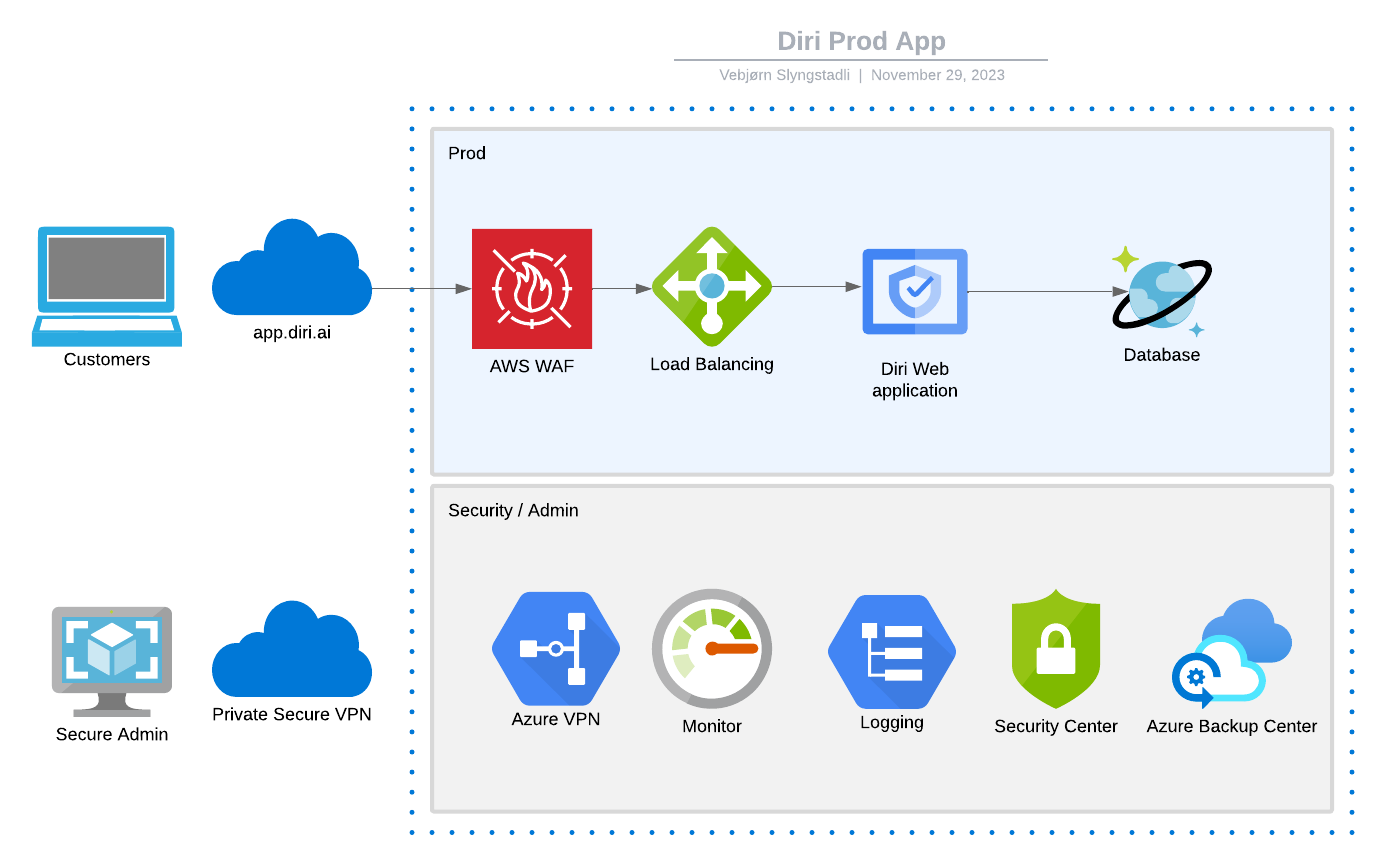
Network security
Our network security and monitoring techniques are designed to provide multiple layers of protection and defence. We use Azure WAF (Web Application Firewall) to prevent our network from unauthorized access and undesirable traffic. Our systems are segmented into separate networks to protect sensitive data. Systems supporting testing and development activities are hosted in a separate network from systems supporting Diri's production infrastructure.
We monitor firewall access with a strict, regular schedule. A network engineer reviews all changes made to the firewall regularly. Diri monitors the infrastructure and applications for any discrepancies or suspicious activities. All crucial parameters are continuously monitored using our proprietary tool and notifications are triggered in any instance of abnormal or suspicious activities in our production environment.
Network redundancy
All the components of our platform are built to be redundant. If there's a server failure, users can carry on as usual because their data and Diri´s services will still be available to them.
Intrusion detection and prevention
Our intrusion detection mechanism takes note of host-based signals on individual devices and network-based signals from monitoring points within our tenant. Administrative access, use of privileged commands, and system calls on all servers in our production network are logged. Rules and machine intelligence built on top of this data give security engineers warnings of possible incidents. At the application layer, we have our Azure WAF
Data security
Secure by design
Every change and a new feature is governed by a change management policy to ensure all application changes are authorized before implementation into production. Our Software Development Life Cycle (SDLC) mandates adherence to secure coding guidelines, as well as a screening of code changes for potential security issues with our code analyzer tools, vulnerability scanners, and manual review processes.
Our robust security framework based on OWASP standards, implemented in the application layer, provides functionalities to mitigate threats such as SQL injection, Cross-site scripting, and application-layer attacks.
Data isolation
Our framework distributes and maintains the cloud space for our customers. Each customer's data is logically separated from other customers' data. This ensures that no customer data becomes accessible to another customer.
The data is stored on our servers when you use our services. Your data is owned by you, and not by Diri. We do not share this data with any third party without your consent.
Encryption
In transit: All customer data transmitted to our servers over public networks is protected using strong encryption protocols. We mandate all connections to our servers use Transport Layer Security (TLS 1.2/1.3) encryption with strong ciphers, for all connections including web access, and API access to our mobile apps. This ensures a secure connection by allowing the authentication of both parties involved in the connection, and by encrypting data to be transferred. We have enabled strict forwarding to HTTPS in our Web Application Gateway to all our web connections. This tells all modern browsers to only connect to us over an encrypted connection, even if you type a URL to an insecure page at our site. Additionally, on the web, we flag all our authentication cookies as secure.
At rest: Customer data at rest is encrypted using 256-bit Advanced Encryption Standard (AES), one of the strongest block ciphers available, and is FIPS 140-2 compliant. The data that is encrypted at rest uses
Platform-managed keys.
Please click here for detailed information about encryption at Diri.
Data retention and disposal
We hold the data in your account as long as you choose to use Diri Services. Once you terminate your subscription to Diri services, your data will get deleted from the active database during the next clean-up which occurs once every six months. The data deleted from the active database will be deleted from backups after three months. In case your unpaid account is inactive for a continuous period of 120 days, we will terminate it after giving you prior notice and the option to back up your data.
Identity and Access control
Single Sign-On (SSO)
Diri offers a single sign-on (SSO) that lets users access multiple services using the same sign-in page and authentication credentials. At the moment, Diri supports integration with
Microsoft Azure AD.
SSO simplifies the login process, ensures compliance, provides effective access control and reporting, and reduces the risk of password fatigue, and hence weak passwords.
Multi-Factor Authentication (MFA)
MFA provides an extra layer of security by demanding an additional verification that the user must possess and the password. This can significantly reduce the risk of unauthorized access if a user’s password is compromised. You can configure multi-factor authentication by enabling it on your Microsoft Azure AD Account.
Read more about Microsoft MFA.
Administrative access
We employ technical access controls and internal policies to prohibit employees from arbitrarily accessing user data. We adhere to the principles of least privilege and role-based permissions to minimize the risk of data exposure.
Access to production environments is maintained by a central directory and authenticated using a combination of strong passwords, two-factor authentication, and passphrase-protected SSH keys. Furthermore, we facilitate such access through a separate network with stricter rules and hardened devices. Additionally, we log all the operations and audit them periodically.
Operational security
Logging and Monitoring
We monitor and analyze information gathered from services, internal traffic in our network, and usage of devices and terminals. We record this information in the form of event logs, audit logs, fault logs, administrator logs, and operator logs. These logs are automatically monitored and analyzed to a reasonable extent that helps us identify anomalies such as unusual activity in employees’ accounts or attempts to access customer data. We store these logs in a secure server isolated from full system access to manage access control centrally and ensure availability. Click here to see the current status of our services.
Detailed audit logging covering all update and delete operations performed by the user is available to the customers in every Diri service.
Vulnerability management
We have a dedicated vulnerability management process that actively scans for security threats using a combination of certified third-party scanning tools and in-house tools and with automated and manual penetration testing efforts. Furthermore, our security team actively reviews inbound security reports and monitors public mailing lists, blog posts, and wikis to spot security incidents that might affect the company’s infrastructure.
Once we identify a vulnerability requiring remediation, it is logged, prioritized according to the severity, and assigned to an owner. We further identify the associated risks and track the vulnerability until it is closed by either patching the vulnerable systems or applying relevant controls.
Malware and spam protection
We scan all user files using our automated scanning system that’s designed to stop malware from being spread through Diri's ecosystem. Our anti-malware engine receives regular updates from external threat intelligence sources and scans files against blacklisted signatures and malicious patterns.
Diri supports Domain-based Message Authentication, Reporting, and Conformance (DMARC) as a way to prevent spam. DMARC uses SPF and DKIM to verify that messages are authentic.
Backup
We run full backups every day in Microsoft Azure. Backup data is stored in the same tenant and encrypted using AES-256 bit algorithm. All backed-up data are retained for a period of three months. If a customer requests data recovery within the retention period, we will restore their data and provide secure access to it. The timeline for data restoration depends on the size of the data and the complexity involved.
Disaster recovery and business continuity
Application data is stored on resilient storage that is replicated across data centres in Microsoft Azure.
Incident Management
Reporting
We have a dedicated incident management team. We notify you of the incidents in our environment that apply to you, along with suitable actions that you may need to take. We track and close the incidents with appropriate corrective actions. Whenever applicable, we will identify, collect, acquire and provide you with necessary evidence in the form of application and audit logs regarding incidents that apply to you. Furthermore, we implement controls to prevent the recurrence of similar situations.
We respond to the security or privacy incidents you report to us through
security@diri.ai with high priority. For general incidents, we will notify users through our blogs, forums, and social media. For incidents specific to an individual user or an organization, we will notify the concerned party through email (using the primary email address of the Organisation administrator registered with us).
Breach notification
As data controllers, we notify the concerned Data Protection Authority of a breach within 72 hours after we become aware of it, according to the General Data Protection Regulation (GDPR). Depending on specific requirements, we notify the customers too, when necessary. As data processors, we inform the concerned data controllers without undue delay.
Vendor and Third-party supplier management
We evaluate and qualify our vendors based on our vendor management policy. We onboard new vendors after understanding their processes for delivering us service, and performing risk assessments. We take appropriate steps to ensure our security stance is maintained by establishing agreements that require the vendors to adhere to confidentiality, availability, and integrity commitments we have made to our customers. We monitor the effective operation of the organization’s process and security measures by conducting periodic reviews of their controls.
Customer controls for security
So far, we have discussed what we do to offer security on various fronts to our customers. Here are the things that you as a customer can do to ensure security from your end:
- Choose a unique, strong password and protect it.
- Use multi-factor authentication
- Use the latest browser versions, mobile OS and updated mobile applications to ensure they are patched against vulnerabilities and to use latest security features
- Exercise reasonable precautions while sharing data from our cloud environment.
- Classify your information into personal or sensitive and label them accordingly.
- Monitor devices linked to your account, active web sessions, and third-party access to spot anomalies in activities on your account, and manage roles and privileges to your account.
- Be aware of phishing and malware threats by looking out for unfamiliar emails, websites, and links that may exploit your sensitive information by impersonating Diri or other services you trust.
Conclusion
Security of your data is your right and a never-ending mission of Diri. We will continue to work hard to keep your data secure like we always have. For any further queries on this topic, please take a look at our Help Center or write to us at security@diri.ai
support@diri.ai or +47 400 00 343 (8am-4pm)
Related Articles
Secure Software Development Practices
Software security Preventing security incidents and mitigating the risk of security breaches is a foremost priority in Diri AS. We are contiuously working to improve our software security. Secure coding practices Developers follow secure coding ...Data processor agreements
Please contact us for more info contact@diri.ai